
If you had to guess how many emails are sent worldwide daily, what would you say? A few million? A few hundred million? A billion? According to the latest statistics, there are 205 billion emails sent every day. Of those daily emails, 116 billion of them are business emails. That is a lot of correspondence and a lot of opportunities for spammers to try to steal your personal or company information or plant malicious files and software on your computer.
In 2012, a report was done on the cost of spam email to consumers and businesses. Things considered as cost were; the cost of hardware and software purchased to prevent or filter spam, the cost consumers incurred when clicking on links or opening attachments (personal and financial information stolen), and the cost of cleaning up the mess afterward. In 2012 alone, the cost to consumers and businesses was between 20 and 50 billion dollars. On the other side of the spectrum, the spammers purportedly made over $200 million dollars off their victims.
Another report breaks this amount down in a more molecular manner. It states, the cost of spam to the recipient is $0.10 per spam email received. The average office worker receives 90 emails a day. Of those 90 emails, 14 of them are spam. That works out to $1.40 a day for one worker alone. Multiply that times the number of employees in your business and that is the daily cost of spam to your company.
On the flip side, the spammers only spend $0.001 per email sent and they reap all the benefits when a reader gets caught in the trap.
This article will attempt to explain what exactly spam is, how to avoid it, and what to do if you accidentally step in it. Educating yourself about email and security best practices is the best way to protect yourself and your business from undue harm.
What is SPAM email?
Spam is any email the recipient did not request or sign up for, and does not want. Like paper junk mail, some forms of spam are harmless, but annoying. These include the endless stream of offers and ads from businesses you shopped at online once but have never visited again or the newsletters you signed up for once upon a time and now get 3 times a day. These emails are annoying, but they won’t actually cause you or your business any damage. They might slow down your email server or spam filter, but no real harm will be done.
Malicious spam, on the other hand, is crafted with the intention of doing harm to the recipient or the recipient’s network. These emails come in many different forms and most are familiar to us by now, but spammers are constantly evolving their techniques and improving their scams. This means, email users must also constantly evolve and learn new ways to detect spam.
Types of Spam
Non-Malicious Spam:
These are typically, the numerous newsletters, ads, and offers you receive from businesses after visiting their website or online store or after signing up for something. Most of the time, you have either knowingly or unknowingly left a box checked to receive their correspondence. These emails are annoying, and often come way too frequently, but the only harm they tend to cause is making us aware of a new deal or product we didn’t know we needed and must now buy. These are safe to click on as long as you are sure it is from a business or service to which you subscribed. Most of the time, they provide an unsubscribe button at the bottom of the email so you can stop the onslaught of emails if you choose. A better way to unsubscribe to these emails is to visit the website on which you signed up, and edit your email preferences. The reason this is the safer option is because spammers use fake unsubscribe links to phish for your information or confirm they have a live email address. By simply avoiding clicking ANY unsubscribe button or link, you can ensure you never fall in to this type of trap
Malicious Spam:
There are many different types of malicious spam. The major categories are discussed below, but be aware, this list does not cover every type of harmful spam email. Do not assume an email is safe simply because it is not on this list.
Malicious Attachments:
These are some of the most dangerous spam emails you can receive. The goal of the spammer is to get you to open an attachment. When you do, malware, or harmful and damaging software, is automatically installed on your computer. This malware can include; key loggers that track your every keystroke and report it back to the hacker, viruses that damage your computer, malware that causes pop ups and false alerts that try to make you click a link and buy something, and even worms that self-replicate to other computers on your network.
Recently, ransomware has been extremely popular with spammers and hackers. Ransomware is a type of virus that encrypts, or garbles, all of the files on your network making them unreadable and useless. It then gives you an alert in the form of a ransom note. “Pay $200k by 3pm or we will kill your data.” It may sound like the plot of a bad movie, but it really happens and businesses are frequently being hit by this type of attack. And the amounts being demanded are steep. Unfortunately, there are really only 2 ways to deal with this type of attack once it happens; restore everything from a backup or pay. For small businesses without IT support, the backup option is often times not available and they are forced to pay the ransom.
Types of files to watch out for in attachments are:
- compressed folders such as .zip and .rar files
- ANY .exe file
- Microsoft Office files such as .doc, .docx, .xls, and .rtf
- Java and Javascript files (typically hidden inside the zip folders) .js, .jar, .wsf,.wrn
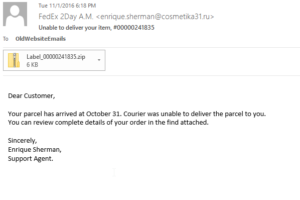 Example of a spam email with a malicious attachment. Notice the sender’s email address is NOT a FedEx address. The .ru at the end means this email address is from Russia.
Example of a spam email with a malicious attachment. Notice the sender’s email address is NOT a FedEx address. The .ru at the end means this email address is from Russia.
Example of a spam email with a malicious attachment. Notice the sender’s email address is NOT a FedEx address. The .ru at the end means this email address is from Russia.
Phishing Spam:
Phishing is a term that is used to describe messages that entice the reader to provide some form of personal information. These may request you click a link, send money, or “confirm” your personal information in some way. These are the “work from home”, “new miracle cure”, and “click here to try” types of emails most of us are used to receiving.
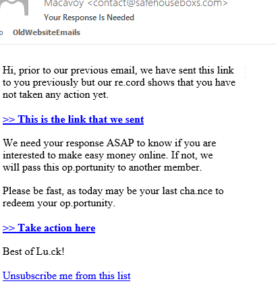 Example of a phishing email. Notice the typos and the vague nature of the “opportunity”. All of the links in this email, including the unsubscribe link, lead to a phishing website designed to steal your personal information.
Example of a phishing email. Notice the typos and the vague nature of the “opportunity”. All of the links in this email, including the unsubscribe link, lead to a phishing website designed to steal your personal information.
Spammers even go so far as to create duplicate websites of popular online stores. These fakes look identical to the original, but instead of giving your credit card info to Apple, you have just handed it to the hackers. The three companies attacked by these scams more often than other companies are Yahoo, Microsoft, and Facebook. Of the companies attacked most, Apple is at 27% and Amazon 21%.
These phishing websites are so good that it is hard to tell the difference between them and the real deal. Pay attention to the domain name (the website address) of the websites you visit and make sure they are correct before entering your banking information.
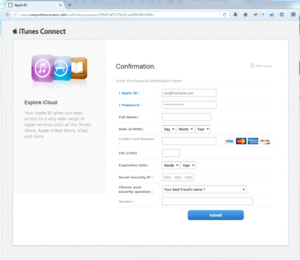 This is an example of a phishing website. It looks identical to the Apple iTunes Connect website. If you look at the website address however, you will see it is NOT an Apple website at all. Look at the information being requested here. A person who fills in this form has now given the hackers everything needed to steal the person’s identity. Since most people use the same “security question” and password for all websites, by entering this information, the hackers have now gained access to ALL of your information across all websites, not just your Apple ID.
This is an example of a phishing website. It looks identical to the Apple iTunes Connect website. If you look at the website address however, you will see it is NOT an Apple website at all. Look at the information being requested here. A person who fills in this form has now given the hackers everything needed to steal the person’s identity. Since most people use the same “security question” and password for all websites, by entering this information, the hackers have now gained access to ALL of your information across all websites, not just your Apple ID.
Current Event Spam:
Current event spam uses any major news or political events in recent history to attract the user’s attention or sympathy and get them to click a link or open an attachment. These topics include current political events and elections, wars, natural disasters, or anything else that has made the headlines and might bait the reader into clicking the link.
 This is an example of current event spam. ALL of the links in this email, including the image, lead to a website containing malware.
This is an example of current event spam. ALL of the links in this email, including the image, lead to a website containing malware.
A subset of Current Event Spam is Terrorist Spam. These emails tell a story about someone heroic trying to stop terrorism or some poor soul trapped in a terrorist’s web, and these people desperately need your help to stop the bad people of the world. “You’re our only hope!” Or, they are trying to sell you a product they have brilliantly designed that is the end all be all in anti-terrorism technology. “We just need your support!”
Clicking the links on emails like these will most likely result in either malware being installed on your computer or you being asked to enter your personal and financial information into a hacker’s fake website.
Financial Spam:
There are two major types of financial spam. The first is the standard Nigerian prince wanting to send you a few million dollars. These types of emails have been around the longest and surprisingly, thousands of people still fall for these scams every year. The stories vary wildly, but they are all basically the same. Someone has tons of money, but they cannot access it due to some unjust overlord or evil banking or government system and they need your assistance to help them get the money. “If you just give my attorney your bank account information, the $2 million will be transferred to you and I will let you keep most of it!” What’s the old saying about fools and their money?
The second type of financial spam is fairly new and includes some pretty tricky methods to trap the reader. These emails are usually pretty straightforward and appear professional. They mention an invoice or purchase order number and are requesting the reader take some action to complete the transaction. These emails tend to look real and that makes them dangerous. Some of these emails will say the company, many times one you actually do business with, is updating records and needs your newest information. Others will again reference a company you are familiar with and a PO or invoice number and request you send them data or click a link to complete the transaction or purchase. Some even attach the referenced PO or invoice for your review. The attachment is, of course, malware.
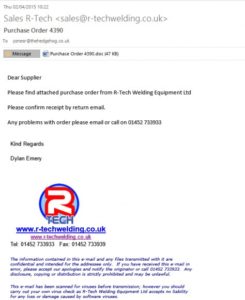 Example of a PO containing malware. This email looks extremely legitimate, but the attachment contains malware.
Example of a PO containing malware. This email looks extremely legitimate, but the attachment contains malware.
If you receive one of these and are not quite sure if it is spam, do not open the attachment or click the link. Look up the PO or Invoice number in your company software to see if the referenced company is indeed associated with that invoice. Try to verify the contents of the email in your own internal software before dealing with the email. If you are still unsure, call the company in question and speak with someone about the issue before opening the attachment.
Foreign Company Products or Services:
These spam messages are typically a data sheet of products offered or details about a great new product. The company is always foreign and typically Chinese or Indian. All of the links to their products or services go to a fake website that phishes for your information.
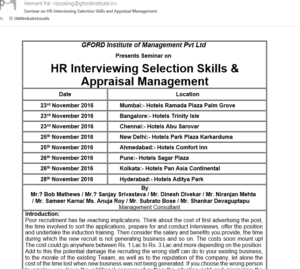 Example of a Foreign Company Service spam email.
Example of a Foreign Company Service spam email.
The email in this example looks fairly legitimate, but notice all the grammar issues and typos in the image above. In the image below, notice the request for payment PRIOR to the event and that the email address to book seats to the seminar is not the same domain as the one that sent that email. It is not even a business address, but a Yahoo address. A quick Google search of the GFORD Institute of Management Pvt Ltd reveals the company does in fact exist as a business entity in New Dehli India, but they have no website. Their Facebook page also has nothing but spam posts and complaints from people demanding the company stop spamming them.

Notice the Yahoo address and request for money to be mailed to them upfront. Since this “Institute” has no website, I highly doubt this seminar is real. Besides, who would attend an Interview and Management training seminar from a group with such poor grammar and no website? Even kids have websites these days.
How to Avoid SPAM
Now that you are familiar with the types of spam and can more easily identify them, let’s discuss how to avoid getting spam in the first place.
General Security Tips
Strong Passwords
The first step in securing your home is typically shutting and locking the doors, right? Why pay for an expensive security system if you leave all the doors wide open? The same is true for your internet security. The first step in keeping your personal and business information safe is a strong password.
So how strong is strong and what does that look like? The strongest password is always going to be a string of random numbers, letters and symbols. Unfortunately, these are also the most difficult to remember. A better suggestion is to find a sentence you can easily remember, change a few of the letters to numbers or symbols and use this as your password. For example: “Th3 bl@ck D0g runs”. This sentence is in no way personal to the user and so cannot be guessed by anyone easily. It also contains several numbers and symbols as well as upper and lower case letters. All of this combined makes it much more difficult for hackers to figure out your password and break into your system. However, this is still understandable enough for the user to remember easily.
Never Share Your Password with Anyone
What is the point of locking your valuables in a safe and then handing random strangers the key? You do the same thing every time you give someone your password. Especially if you use the same password for everything.
Never share your password unless absolutely necessary. If you do have to share your password for some reason, immediately change it afterward. This includes your IT department and help desk people. If you require support on your computer or a website, make sure you are there to enter the passwords personally.
In addition to accessing your personal information, providing someone easy access to your password allows them to access your system and websites as you and any changes made or harm done would appear as if YOU made them.
Unsecured Websites
Never send private information through unsecure websites. How can you tell if a website is secure? In front of every website address is either http:// or https:// . The “s” on the end of the second one means secure. If you do not see the “s”, the website is not secure.
Does this mean that any unsecured website is bad? Not necessarily. It simply means the secured websites have been verified to be who they say they are. Sometimes you will see a warning when you visit a website. This warning might say something about a website’s security certificate. The safest bet is to not continue on to the website unless you know for a fact it is safe. If it is a website you are not familiar with or it is a website you visit frequently and this is a new warning, leave immediately. Just like road signs, these warnings are there for your safety but they only work if you abide by them.
Anti-Virus Software
Install and use anti-virus software. One of the biggest mistakes people make is purchasing and installing anti-virus software and assuming they are protected. This software must be configured to run regularly for it to be useful. Set your software to run daily quick scans and monthly or weekly full scans. You should also make sure your AV software is scanning files and attachments when they are opened, especially in your email.
Keeping Your Software Up to Date
Lastly, make sure to keep your operating system and other software on your computer up to date. As developers find security holes in their software (or hackers find the holes for them), updates are released to fix these issues. By not updating your computer regularly, you leave yourself vulnerable to people exploiting these weaknesses.
SPAM Dos and Don’ts
- Don’t click on links in emails unless you are certain they are safe
- Don’t open attachments from people you were not expecting attachments from or from which you do not normally receive attachments
- Never reply to a SPAM email or click the unsubscribe link. This verifies your email address as valid and you will end up with more spam.
- Do not give your email address out online. This includes forums and social media profiles where your email will be visible to the public and can be harvested by spammers.
- Do not sign up for newsletters or websites unless you are sure it is a legitimate business.
- Don’t make your username the same as your email address. A lot of spammers are really good guessers. Don’t make it easy for them.
- Do pay attention the TO and FROM addresses. If they look suspicious or fishy, assume it is spam.
- Do pay attention to the subject line and body. If they do not match or seem odd, assume it is spam.
- Do pay attention to the other people on the email. If you were cc’d on an email with people you do not know, or the other names on the TO list seem odd (all start with the same letter or are all similar), assume it is spam.
- Do pay attention to the grammar and typos. This is a big indicator of spam.
- Do Google the company, sender’s email address, or subject before taking action. If it is spam, most likely Google will tell you.
- Do research before clicking on anything. Search through your internal software for any connection such as an invoice before opening the attachment.
- Do feel free to call the company if it is one you are familiar with and ask if they sent the email before clicking anything.
So You Stepped in it…Now What?
We have learned what spam is and how to avoid it, but what should you do if you are already getting spam or you accidentally click on something in a spam email? Don’t panic. Spam might be messy, but it can be cleaned up.
The first recommendation is to install a spam filter. This is hardware or software that sifts through all emails coming into your email server and filters out the spam. This is vital for businesses, but is also available as software for individuals. Most good firewall software these days comes with some sort of spam filtering built-in. It will take a bit of playing with in the beginning to get the settings just right, but in the end, a filter will be the best tool for blocking the spam before it gets to your inbox.
Next, you need to make sure to run your antivirus program on a full scan to clean any viruses that might have been installed by the malicious spam. If you are seeing pop-ups or fake alerts on your computer, chances are you have been infected.
For ransomware alerts, those threatening pop-ups demanding money for the release of your data, immediately disconnect your computer from the network; unplug your network cable and turn off the Wi-Fi adapter. This will help prevent the ransomware from spreading to other computers on your network. Then immediately notify your IT support for assistance.
The most important thing to stop spam emails is to report them. Spam filters typically have built-in means of reporting spam. These reports help the filter to learn what is and what is not spam. By reporting every instance of spam, you are helping the system get better at filter out the garbage for all users. Contact your IT people to learn how to report spam inside your organization.
If your organization does not have spam filtering, there are public and government services to whom you can report spam. One such service is SpamCop. When you report an email to SpamCop, the service will send warning information to the Internet Service Provider of the offender alerting them to the improper use of their service. Most ISPs will block the spam with enough reports. SpamCop also adds the spammer to a block list. This service is free.
The Department of Justice has multiple means of reporting spam emails. In addition to tips about dealing with spam, where to report can be found at https://www.justice.gov/doj/spam.
Hopefully, the tips and information found in this article will help you to reduce the amount of spam you receive and the damage caused by that spam. Now that you know what to look for, you should be able to more easily identify spam and avoid it, or at the very least reduce the amount you receive. And remember, the spammers are always adapting and changing so you must too!
Don’t forget to check out our other blog posts and as always, we appreciate you sharing our posts on social media.


